What is a RAT?
- August 22, 2019
- Posted by:
- Categories: Archer News, Ask Archer, Cyber Crime, Cyberattack, Hacking, Industrial Control System Security, Posts with image, Power Grid

RAT stands for “remote access Trojan.”
Attackers put a RAT on your machine so they can get remote access — observing you and controlling you from far away.
You don’t want a RAT on your system!
Watch here:
Sneaky RAT
Attackers will try to trick you into installing their RAT, a sneaky, evil program that hides itself away.
How do they do it?
Often, through your inbox.
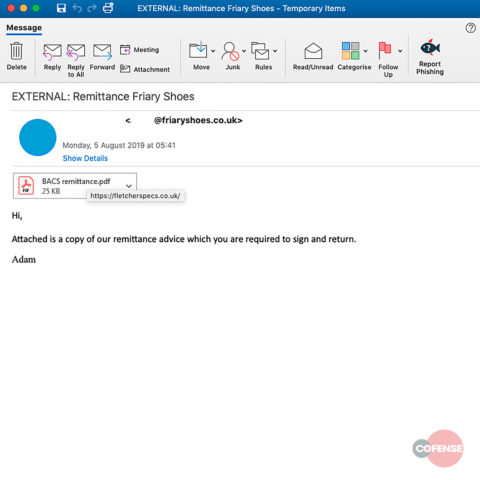
In one of the latest cases, Cofense reports bad guys are sending emails to utilities in the U.S.
The emails say, “Attached is a copy of our remittance advice which you are required to sign and return.”
The sender? Friary Shoes in the U.K.
But it’s a fake — some hacked a real Friary Shoes account to send out the emails.
Click on the attachment and you’ll end up with a remote access Trojan, according to Cofense.
The malware, known as SockRAT, jRAT, and Adwind, takes screen shots, steals passwords, takes pictures and video through your web cam, transfers files, watches your every keystroke and more.
Big Targets
Experts say the bad guys often try to install RATs on work computers, to spy or to steal money and passwords.
But sometimes they want more.
In July, companies in the utilities sector received phishing emails from what looked like a U.S. engineering licensing board, according to Proofpoint.
The realistic-looking emails notified the engineers that they had failed their recent licensing exam.
But click on the test results attachment, and the engineers that help run the nation’s power grid would download a RAT that could delete files and move and click their mice.
Proofpoint concluded that a nation-state is behind this attempt to infiltrate and control utilities in the U.S.
If an attacker landed a RAT on industrial computers that control big equipment, they could do damage — and even hurt or kill people nearby.

What Can You Do?
Another RAT making the rounds right now uses emails that look like invoices or purchase orders, reported LMNTRIX Labs in ZDNet.
This RAT review is a good reminder that clicking on bad links or attachments can be very dangerous.
Check before opening. Your company may have a policy about clicking.
Also, be careful if you receive a message asking you to install an app or software.
If you’re concerned about your home computer, you can run a malware scan to see if it catches a RAT.
Businesses can monitor their networks for signs of RAT traffic.
If you find a RAT, you may need to rebuild the computer to make sure the malware is truly gone.
For home or business, keeping your devices updated with the latest versions will help.
You may find more help at these sites:
How to remove malware from your PC (PCMag)
What is a Trojan virus? (Webroot)
Trojan Horse Removal: Protecting Troy (Emsisoft)
What malware is lurking around the corner? (Bitdefender)
See more “What is?” questions at Archer News:
What is a DMZ in the digital world?
How long should my password be?
Main image: LEGO rodent with cheese. Image: Ekaterina79
