The hack is coming from inside your chest
- December 1, 2016
- Posted by:
- Categories: Archer News, Cyber Crime, Cyberattack, Hacking, Health Care Security, Posts with image, Smart Devices

New research shows how bad guys can get in through a security hole in pacemakers & other heart-saving devices.
A man with a backpack, standing near the ring of security around a Very Important Person.
There’s no bomb or gun inside that pack—nothing to confiscate—just medical equipment.
Still, the killer can launch a deadly attack—by zapping the VIP’s pacemaker from 15 feet away, according to researchers who have uncovered the potentially murderous hack.
“The consequences of these attacks can be fatal for patients as these messages can contain
commands to deliver a shock or to disable a therapy,” international researchers from KU Leuven University and University Hospital Gasthuisberg Leuven in Belgium and the University of Birmingham in England said in their paper.

An example of a pacemaker. The researchers did not specify which implantable devices they hacked, and there is no evidence to suggest this is one of the models they examined.
New developments
Other researchers have hacked pacemakers before.
Former Vice President Dick Cheney cut off the wireless communication from his heart defibrillator that was implanted in 2007 so that terrorist could not attack him from the inside out.
But the researchers said their work shows some new developments in the world of medical device security and insecurity.
Malicious hackers can attack from much further away than before, the paper said.
It also said at least ten current types of devices, called Implantable Cardioverter Defibrillators or ICDs, are vulnerable.
And it may be too easy to carry out—attackers don’t need a lot of expertise on medical equipment to cause serious problems, researcher Dave Singelée with KU Leuven University told Archer News.
“So this shows that a hacker, with some basic knowledge on electronics and telecommunication, could indeed perform these steps and learn how to hack medical devices,” he said.

Former vice president Dick Cheney on board Marine Two in 2004, three years before his surgery to implant a pacemaker. Photo credit: The U.S. National Archives via Foter.com / No known copyright restrictions
How it works
The weak point is the wireless communication between the device in your chest and the person who controls it.
Wireless communication lets the doctor change or update your pacemaker or other device without surgery. But it also gives an attacker a way in, if it is not protected properly, the researchers said.
Used properly, the devices can give your heart a therapeutic shock if it is beating too slowly or quickly.
But this kind of attack could let the attacker impersonate the doctor and send their own vicious message, according to the paper.
They could send the same message over and over, or drain your battery, so the device doesn’t work at all.
And some of the medical equipment is available online on places like eBay, the researchers noted.
New & improved
Older versions of these pacemakers and devices had a very short wireless distance—about four inches.
But newer versions have a longer-range distance—up to about 15 feet, the researchers explained.
“Therefore, an adversary could only exploit this when being very close to the victim,” Singelée said to Archer News. “This limits the practical impact of such attack.”
But newer versions have a longer-range distance—up to about 15 feet, the researchers explained.
“Our attacks are possible on the long-range communication, which is a feature present in the more recent versions of ICDs,” said Singelée. “Therefore, an adversary now could be further away when carrying out the attack.”
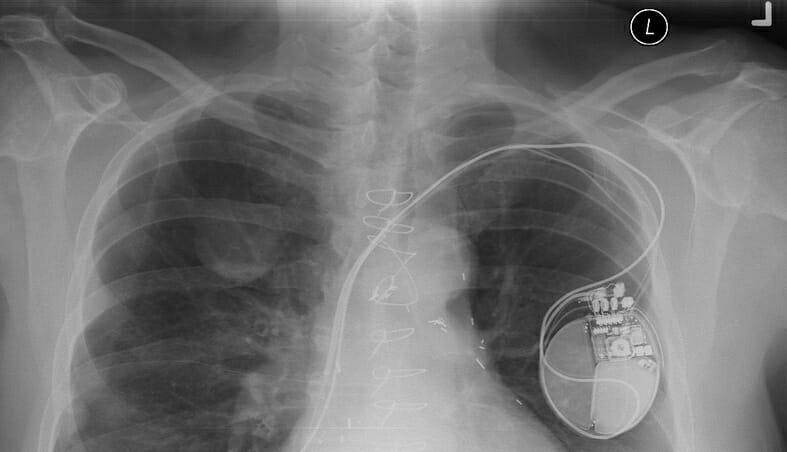
A chest X-ray showing an implanted medical device. Photo credit: Pulmonary Pathology via Foter.com / CC BY-SA
Open window
The pacemakers and devices are not vulnerable at all times, the team said.
But after a doctor makes changes to a person’s device through the wireless channel, the devices stay open for some time before shutting down.
That window gives the attacker time to jump in and tell your pacemaker to do you harm, or to keep extending that window to give him or her more time to carry out a longer attack.
Spying on you from the inside
Spies could use the same kind of security hole to listen in on the communication between you and your doctor, and find out the state of your health, what kind of therapy you’re getting, and other sensitive info.
“For example, adversaries could install beacons in strategic locations (e.g. the train station or the hospital) to infer the patients’ movement pattern based on the signals transmitted by their ICDs,” researchers wrote.

Electronic monitoring of a patient’s heart.
Solutions
The team laid out possible solutions to protect people with pacemakers, and notified the manufacturer about the problem.
Device makers need to add more advanced security solutions than they currently have, said Singelée.
“Our research clearly shows the need to add cryptography to medical implants, to secure their wireless connection,” he said. “Our research results show that it is feasible to add lightweight cryptographic solutions to these devices.”
Short game & long game
Device makers need to make one change right away, according to the team—block wireless communication during the window after the doctor finishes adjusting a person’s treatment, so an attacker can’t slip in.
“As a short-term countermeasure, the only solution is to use jamming as a defensive mechanism,” they said.
Another change should come as manufacturers put out new versions of their devices, they said. Doctors should be able to send a “shutdown” message after they are done so that the window closes and the patient is safe.
The research team also wants manufacturers to use a better way of checking to make sure the messages coming in to the device are really from the doctor and not a bad guy.

An office display showing pacemakers from 1980 to 2000. The researchers did not specify which implantable devices they hacked, and there is no evidence to suggest this company makes any of the models they examined. Photo credit: jurvetson via Foter.com / CC BY
Blueprint for evil?
Could an attacker follow the details in the paper and assassinate a prime minister or president with a pacemaker—or even a neighbor down the block?
No, said Singelée.
“Some important details are left out of our paper, to ensure that people with bad intentions cannot immediately use our results to hack someone’s pacemaker in real life,” he said.
But that does not mean malicious hackers have not already come to the same conclusion as the researchers have—that some heart-saving devices leave people in a dangerous spot.
“Of course, a hacker spending some effort to repeat our experiments—which he could already have done before our paper appeared, since attacks on ICDs have been reported before—could start doing this in real life,” Singelée said.

The Showtime series Homeland told the story of a vice president who died after terrorists hacked his pacemaker. Photo credit: Leaphart3 via Foter.com / CC BY-ND
Your heart
What about you and your family—should you be concerned?
“A person that has a pacemaker and is walking on the street should not immediately worry that he/she will be attacked,” Singelée said.
A killer would have to go through a number of somewhat complex steps to make the attack successful, so there are “practical limitations,” he added.
Still, the researchers want device makers to pay more attention to security and take steps to protect the people whose lives depend on them—the man-with-the-backpack scenario may not be real, but the security issues are.
“Overall, it is clear that the consequences of all these attacks can be severe for patients,” they said.
