Did cyber ‘ghost’ haunt beauty site?
- May 18, 2017
- Posted by:
- Categories: Archer News, Cyber Crime, Data Breach, Hacking, Posts with image

Undercover criminals intercepted credit card payments at high-end cosmetics store online, the company reported.
For some, it’s a guilty pleasure.
They buy ancient Japanese beauty secrets in the form of skin cream and moisturizers for as much as $185 a jar.
But customers of the Tatcha cosmetics brand have learned that crooks were working on their own secret, lurking on the Tatcha site and stealing credit card numbers as people went to pay.

Example of a Tatcha online shopping cart from Tatcha.com.
The company told customers that an intruder pilfered cards numbers, e-mail addresses, names and Tatcha account passwords intermittently between February 7, 2017 and April 2017.
“Although we do not know if your information was accessed, we do recommend that you contact your credit or debit card company or bank to request a new card number,” Tatcha said in a series of breach FAQs.

Example of Tatcha products. Image via: Tatcha
The company also said if you use your Tatcha password for other accounts on line, you should change those as well.
“The protection of our customers’ personal information is our primary concern and we deeply regret that our online checkout system was compromised,” Tatcha said in a statement to Archer News. “After detecting unusual activity, we took immediate steps to identify and contain the intrusion, and we reported the matter to law enforcement.”

Example of a Tatcha checkout page at Tatcha.com.
Ghost?
Tatcha did not describe how the crooks got in.
But the scenario sounds similar to a new report of malicious cyber ‘ghosts’ haunting websites around the world, waiting for customers to drop in their credit card numbers.
“A bad actor has upped the stakes in his campaign to collect consumer payment card information by expanding his reach,” said The Media Trust, a company that offers monitoring and security for the online and mobile ecosystem.
That reach covers a number of online companies selling beauty products, clothing, home goods and sporting event registrations in the U.S., England and India, the company said in a post.
Tatcha customers are not the only ones who may need new credit cards.
How it works
You see something you want on a site, and you go to enter your credit card number.
In the ‘ghost’ scenario, the cyber thief puts a transparent page over the credit card form, according to The Media Trust.
You type in your card number, not realizing that you actually put it on the ghost page, and not on the real page.
“The payment-stealing malware activity is not readily apparent to the average shopper,” said Chris Olson, CEO of The Media Trust.

How the malicious hackers executed the transparent overlay on a payment page, according to The Media Trust. Image credit: The Media Trust
Stolen
Your credit card number goes to the bad guys, not to the site.
The site thinks you’ve made a mistake and sends you an error message or a request to re-submit.
You do it again, and the site finally gets your credit card info.
You may pay twice — once for the actual item, and again when thieves use your debit or credit card to go on a spree.
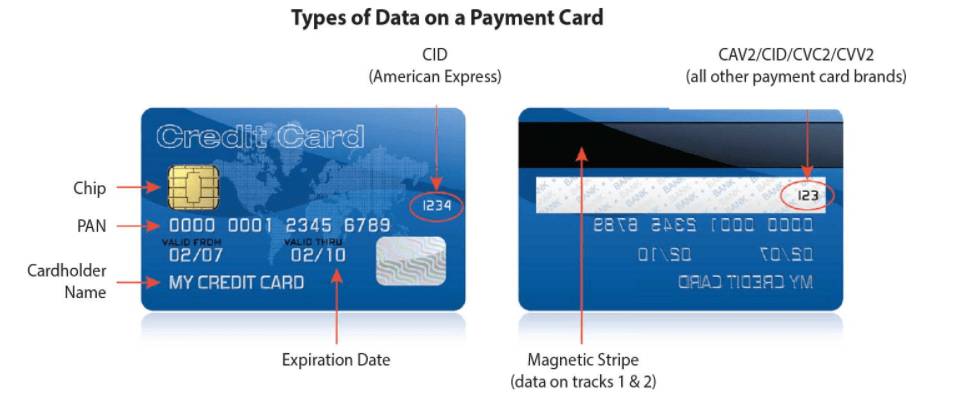
Some of the info thieves want from your credit card, according to the PCI Security Standards Council. Image credit: PCI Security Standards Council
How they get in
Part of the problem, Olson said, is that some ecommerce sites are using an open-source platform, where people can collaborate to develop the code.
That can be good and bad.
“Open-source platforms rely on a passionate community of users to build plug-ins and extensions which extend the capability of the free tool,” Olson said to Archer News. “A major shortfall is that open source lacks the protection users expect — there’s no accountability for the developer community should something go horribly wrong.”
“Bad actors easily infiltrate these communities and cause considerable harm,” he added.
The crooks can quickly burrow into thousands of ecommerce sites and commit crimes like steal credit card numbers, download malware onto a shopper’s system, deface the site or even shut it down, Olson said.
In this latest campaign, the attackers were able to get in, put in their own malicious code, and skulk until an unwitting customer tries to pay, according to Olson.

A warning to small businesses about how malicious hackers can attack payment systems from the PCI Security Standards Council. Image credit: PCI Security Standards Council
What to do
How can you protect yourself, especially when you can’t see the ghost in the machine?
“When transacting on the Internet, consumers should always pay attention to privacy and security policies and overall functionality quirks,” Olson explained.
“It’s a personal judgement call,” he added. “For example, a site that takes too long to load, doesn’t properly display images or has trouble responding to actions (i.e., data input) would be suspect to many.”
Standards
You can also ask or check to see if an ecommerce site if it is compliant with credit card industry standards that protect you from fraud.
The payment card industry created the Payment Card Industry Data Security Standards, or PCI DSS, that every business processing credit card info is supposed to follow.
Amazon Web Services, for example, announces that it is PCI DSS compliant, as do Shopify and Square.

Some security tips for small businesses from the PCI Security Standards Council. Image credit: PCI Security Standards Council
“[A]n informed shopper would carefully read the security policies on every website before making a transaction and see that many of these smaller, boutique ecommerce sites do not have extensive security practices,” Olson said.
You can also check to see if the ecommerce site shows HTTPS in the address bar, a sign that it’s using a more secure system, and see how they’re promoting their adoption of security protocols and privacy-protecting certifications, according to Olson.
“Shoppers should be wary of smaller, boutique ecommerce shops that do not elaborate on their approach to securing online payments,” he explained.

Look for the “https” in the address bar — as you see here on the Smithsonian site — to see if the site is using encrypted communications for your payment.
Not enough?
Unfortunately, even if a site you’re shopping on is compliant with current payment card industry security standards, it may not be enough, Olson said.
He wants to see the standards updated.
“Online transactions remain a risky endeavor,” said The Media Trust in its post.
The Media Trust said it has a policy of not revealing the names of websites that are currently under attack.
If you think you’ve shopped at a site that could be compromised, monitor your debit or credit account to see if you get suspicious charges.

A malicious domain name in a website’s footer. Image credit: The Media Trust
Tatcha
We do not know if the lurkers described by Olson hit Tatcha, too. Tatcha did not respond to that question.
We also don’t know if Tatcha’s site security is lacking or robust.
Either way, the company said it’s making changes.
“We take our obligation to protect customer information very seriously, and have taken steps to further protect your information,” Tatcha told customers. “We are also implementing additional safeguards to make the platform more secure.”

Tatcha tweet via Twitter.
The company’s statement to Archer News went a little further.
“We took down our site temporarily to perform maintenance and make sure the issue is taken care of, and are conducting an internal review of our systems to help further harden our defenses against similar attacks in the future,” Tatcha’s statement said.
