- May 12, 2017
- Posted by:
- Categories: Archer News, Cyber Crime, Cyberattack, Hacking, Posts with image, Ransomware

What is happening and what to do about it.
You can watch the map live, as the ransomware some call “WannaCry” attacks computer systems around the world — and close to home.
San Francisco, Los Angeles, Florida, Texas.
The pulsating dots show where the “bombs” are dropping in real time.
This WanaCrypt0r ransomware has hit more than 75,000 times in 99 countries so far, according to cybersecurity company Avast.
***UPDATE 5-13-17 at 4:48 pm PT*** Avast now reports more than 126,000 hits in 104 countries.
***UPDATE 5-15-17 10:17 am PT*** Avast is now reporting more than 213,000 detections in 112 countries.
In England, doctors at sixteen hospital systems were shut out of their computers, with patients diverted to other medial centers.
A medical worker said patients would “almost certainly suffer and die” because of the attack, the BBC reported.

In Spain, hundreds of computers at one of the country’s biggest communications companies, Telefonica, were infected with the ransomware.
“[T]he company blasted warnings through audio speakers inside their Madrid headquarters, warning employees to shut down their computers,” reported cybersecurity site BleepingComputer.
Other victims reportedly include FedEx and the Russian Interior Ministry, among many others around the globe.
“This is by far the largest ransomware attack the world has seen to date and this could just be the beginning,” said Paul Norris, Tripwire’s senior systems engineer for the Europe, Middle East and Africa region.
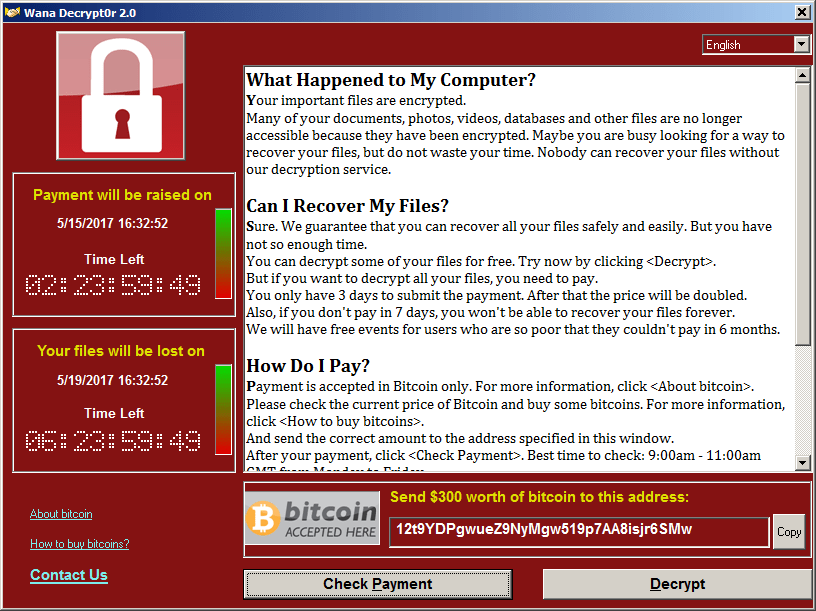
Ransom note from “WannaCry” ransomware. Image credit: Avast
WannaCry
If it hits you, you could see a ransom note on your screen.
Your files will be locked up until you pay $300 in bitcoin, the note says.
Avast researchers saw an uptick in the WanaCrypt0r 2.0 ransomware at 8 am Central European Time today (2 am ET and 11 pm PT).
The activity “quickly escalated into a massive spreading, beginning at 10 am [Central European Time],” Avast’s Jakub Kroustek wrote in a post, where he calls the ransomware “WCry.”

The ransomware is bombarding mostly Russia, Ukraine and Taiwan, but other countries are under fire, too.
“We saw the first version of WanaCrypt0r in February and now the ransomware is available in 28 different languages, from languages like Bulgarian to Vietnamese,” Kroustek said.

“WannaCry” ransomware changes your wallpaper to this screen. Image credit: Avast
How it gets in
This strain of ransomware gets into your computer through a vulnerability in Windows, reports said.
Microsoft issued an update to fix it in March, but not everyone has updated their systems.
In addition, the hacker group ShadowBrokers made the vulnerability — and the method to exploit it — public last month, when they released information on National Security Agency cyber spy tools.
Some call the exploit EternalBlue or DoublePulsar.
Kroustek said that’s most likely how the WanaCrypt0r 2.0 ransomware is spreading.
“This attack once again proves that ransomware is a powerful weapon that can be used against consumers and businesses alike. Ransomware becomes particularly nasty when it infects institutions like hospitals, where it can put people’s lives in danger,” Kroustek said.

“WannaCry” ransomware puts this note into a text file, according to Avast. Image credit: Avast
Still spreading
WannaCry will probably spread to companies in the U.S. as well, security architect Kevin Beaumont told CNN.
The ransomware hunts for other computers on the same network and infects them, too, he said.
“So, for example, if your laptop is infected and you went to a coffee shop, it would spread to PCs [personal computers] at the coffee shop. From there, to other companies,” he said to CNN.

A Twitter user posted a picture of ransomware affecting a transportation system in Germany today.
What if it hits you?
Ransomware encrypts your files, then demands money for the key to decrypt them.
There are some versions of ransomware that you can decrypt on your own, without paying the money.
But this one uses a strong encryption method, security company Malwarebytes said in a post.
“That means that decryption will be next to impossible, unless the coders have made a mistake that we haven’t found yet,” said Pieter Arntz.

What to do now
If you have not been hit, experts urge you to plan and protect yourself.
Check to see if you have patched the vulnerability on your computer and/or computer systems.
If not, patch it right now, disconnect it from the Internet, or shut it down.

“PATCH NOW EVERYWHERE,” warned security architect Kevin Beaumont today on Twitter.
“It’s essential we act immediately to help prevent these attacks,” Norris said to Archer News. “It’s evident that those organisations who have weakened controls have been the main victims of this significant attack.”
Spain’s National Cryptological Center issued a warning labeled “high alert” with these recommendations:
—Find out which systems in your network are susceptible to attack through this vulnerability and isolate, update or shut them down.
—Update all systems to the latest version or patch as recommended by the manufacturer.
—For systems without support or patch available, it’s recommended to isolate from the network or turn it off as appropriate.
—Isolate communication to ports 137 and 138 UDP and ports 139 and 445 TCP in organizations’ networks.
“Keeping devices on current operating systems, hardening systems, updating software and installing security patches might not be exciting, but it’s proven to reduce the number of successful attacks,” Norris said.
